Cyber-Security in 2020 is at the forefront of organizations’ minds across the globe. Cyber-attacks have become more sophisticated and increasingly frequent as businesses and people are relying more and more upon Social Media, Web-based tools and the inter-connectedness of our devices and Apps.
Data Protection (Cyber-Security) used to be only the “IT group’s problem,” but it is now one of the top concerns for Businesses in 2020:
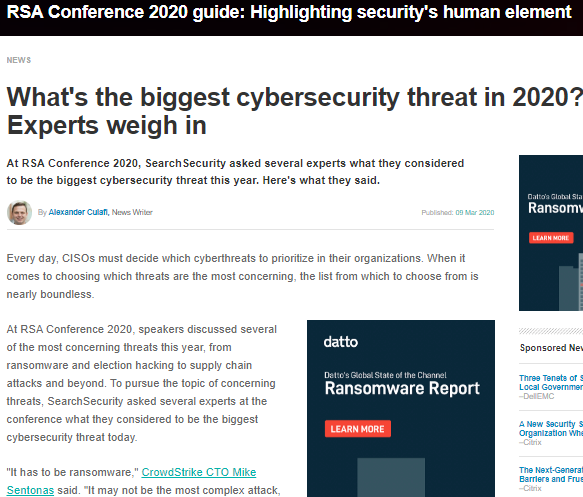
Ransomware is the most prevalent form of Cyber-attacks as it is mostly automated by “bots” and relies upon human error to click things they should not. It is the “easiest” source of money for hackers:
ALL companies, big or small, are now Targets – there are no longer any “focused attacks.”
It is no longer a question of “IF” you will fall victim but “When” …
However, there are some things you can do right now to help reduce your risk of falling victim to Cyber-crime:
Ensure you have regular Off-site Backups
- This is CRUCIAL
- 35% of on-premise backups fail (you cannot restore from them). Either due to old media being used or a damaged external drive, etc.
- Ensure you backup to External media (not just to another drive on the server) AND ensure you have off-site backups.
- Ensure you have multiple levels of backup: Do not just backup your Virtual Servers to external media, you should also be backing up your Database backup files.
Make sure you have a Disaster Recovery Plan in place
Have a strategy for what to do in case of a breach – try to identify interim, short-term and long-term workarounds until you are “back up”. Try to identify timelines.
- Document the Backup and Recovery processes – in case your IT is not available when disaster strikes.
- Identify and Document what to do and who to contact in case of a system crash.
- At least twice a year, perform a full “Test Recovery” of your systems to ensure that it works and that you are aware of all the steps.
Educate your Staff – your first best defence are your people
- Make security practices personal for your users – point out how these best practices can help your staff protect themselves and their families, not just “the business”
- Separate Business from Personal accounts\passwords (especially with Social Media – Facebook, LinkedIn, Twitter, etc and with Banking apps, etc.)
- Never directly open any attachment in an email, skype or text. IF you think it might be safe, then download it to your PC and run it from the PC
- READ pop-ups\messages that appear on your screen and do not just click “yes”. Be aware of what you are responding to, even if it looks harmless.
- Give thought to any responses you are thinking of making to pop-ups, warnings, emails, etc. Does it really make sense? Look at the link you are being asked to visit – does it seem legitimate. If in doubt, do a quick Google search on it – odds are if it is a scam others have likely fallen for it, and there will be posts\warnings.
Consider End-point security
- Do not assume that because something is “on-line” or “in the cloud” that you are completely safe from threat.
- PC\Devices are “ground zero” for most breaches.
- End-point Security packages help prevent potential corruptions from occurring
Revisit and Implement new Password policies
- Enforce password complexity settings and regular password changes – for example:
- Passwords must be 8 characters on more and must contain a mix of Upper and Lower characters and at least 1 non-alpha-numeric character (e.g. T3$t! v. test)
- Passwords should be changed every 3 months – that’s 4 times per year
- The last 4 passwords should be “remembered” by the system and cannot be reused in that time
- Use different passwords for different programs
- Do not “Save” your passwords nor use the “remember me” options on devices.
- Do not send passwords via Email and do not include all the details in electronic communications.
Consider using “Service Accounts” to run key Systems\Services
- Allows you to change the passwords for “logon” accounts (or even disable them) in the event of a breach without impacting your systems directly.
Consider implementing Multi-factor Authentication
- Sometimes also called “Two-factor authentication” or “2fa”
- This is readily available for On-line (cloud-based) O365 systems via the Admin section
- After typing in their passwords, the user must respond to an authorization request on their phone or other device
- You can specify alternate phone numbers and whether you want an App request or a Text.
- There are also 3rd-party tools you can use for Multi-factor authentication with on-premise systems (such as Duo)
Patch your systems regularly
- Microsoft does a lot to help prevent breaches – it can be annoying at times, but it is in your company’s best interest to apply them.
- This goes hand-in-hand with periodic scheduled rebooting of your servers to ensure items are applied fully and to further ensure the systems restart properly.
Ensure you have “Exit procedures” in place for when Employees leave
- Ensure you have a policy for deactivating ex-employee accounts from the Domain, Dbases and any software packages upon their exit.
- This also protects the ex-employee as they can legitimately claim they had no access
Consider Managed Security and Services…
- Managed Security Services allow for more advanced “next-gen” anti-virus\anti-breach tools.
- Pro-active as opposed to the Re-active “Virus Definitions” from most AV programs
- Managed IT Services can also help you to maintain your systems more regularly and provide a pro-active response to potential failures\vulnerabilities
VOX ISM can help too!
3 levels of Security Services:

-
Enhanced Security & End-point Protection
- Protects your Servers, PCs and Tablets from accidental exposure to cyber-threats.
- Applies to Cloud-based users as well as On-premise
- Provides intuitive interface for managing settings and configurations for On-line systems along with pre-configured “template” profile.
-
Secure Backup Protection
- The Secure Backup protection offers Off-site backups to ensure safety of backups and recoverability.
- Applies to Databases and key files\folders for On-premise
- For Cloud-based systems, this includes the backup of O365 Email, Sharepoint and OneDrive files. Dynamics365 users (CRM\BC) already have their Dbases backed up by MS.
- Flexible pricing based on usage is available (based on 50GB\mnth packets).
-
Managed Security & Prevention
- Designed for improved Data-loss prevention.
- Utilizes Advanced Virus and Spam protection including AI-based AV protection software.
- Protects all end-point devices (PCs, Servers, routers etc.).
- Includes Policy-Driven Encryption to help protect against “data mining”.
- Applies to On-line\D365 users as well as On-premise with Windows, MAC and Linux OS.
Join VOX ISM’s Upcoming Events!

Blog post by Trevor Reid – Senior Technology consultant
With over 25 years of experience in the Software and IT Industries (and 20 years with VOX ISM), Trevor has been involved in hundreds of software implementations and upgrades. Currently, he is VOX ISM’s “go to” resource for anything technical having to do with SQL Server, SharePoint, Mobility/IFD, Remote Access, Database migrations and other areas of IT infrastructure and administration. Trevor works closely with our customers and their IT personnel and is always eager to share his wealth of knowledge.
