WARNING: As of Aug. 14, 2019 Microsoft is urging Windows 10 users to update their systems IMMEDIATELY- There are potentially hundreds of millions of vulnerable Computers:
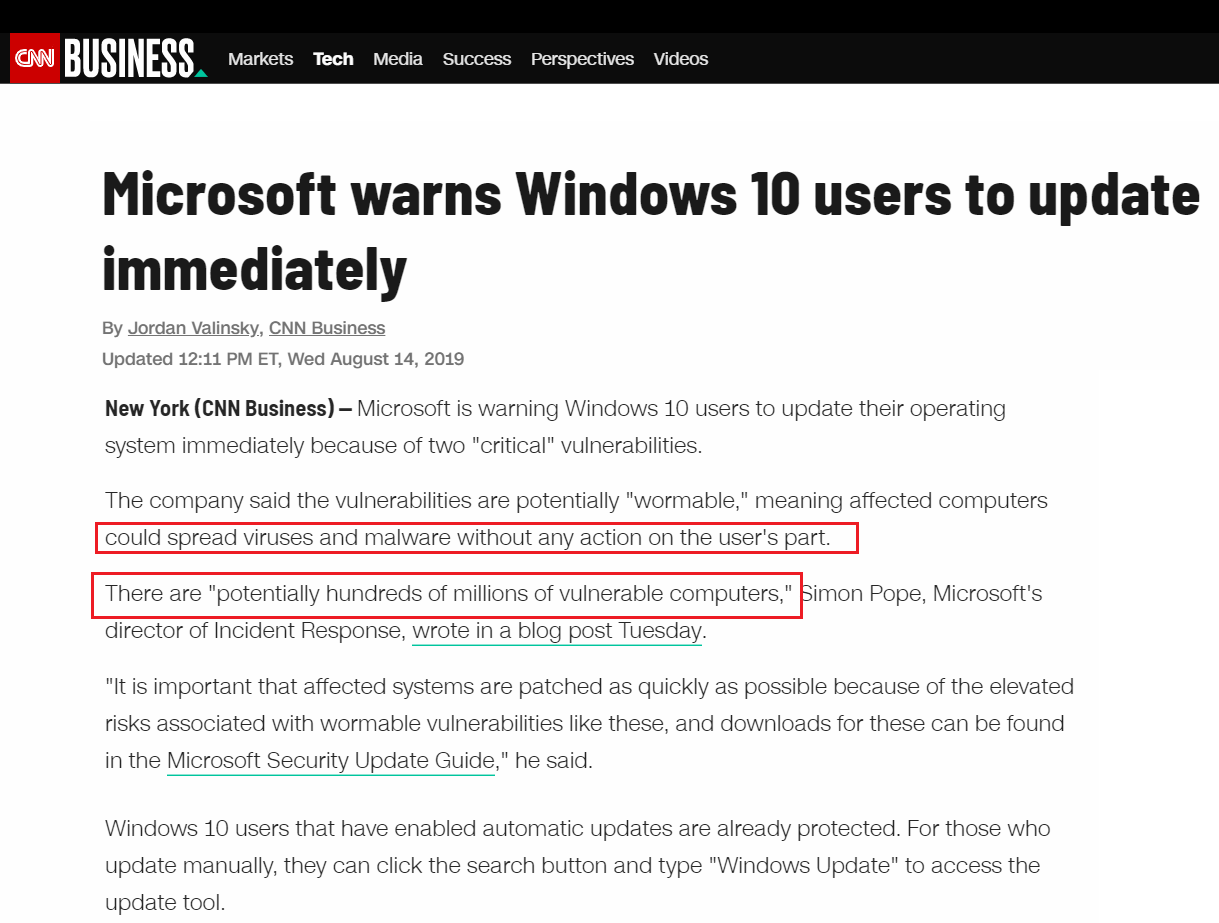
If you are unsure how to apply Windows10 updates, you can look at the process here.
What is Cyber Security?
- Cyber Security is a combination of hardware, software and business practices designed to help mitigate the chances of becoming a victim of “cyber-crime”.
- Most people think of “viruses” when they think of cyber-crime but there are many other forms that cyber-attacks can take.
- Not all cyber-crimes involve stealing data or personal information.
- Ransomware is the most prevalent form of cyber-crime currently and this has been the case since 2017.
What has changed in the past year and what is to come?
- Since 2017 the threat of “cyber-attacks” has not only been increasing at an unprecedented rate but has also become more varied.
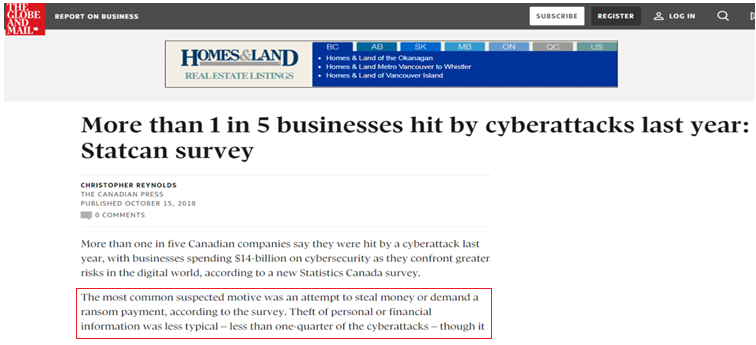
- According to Statistics Canada, in 2017 alone, more than 1 in 5 businesses were hit by cyber-attacks.
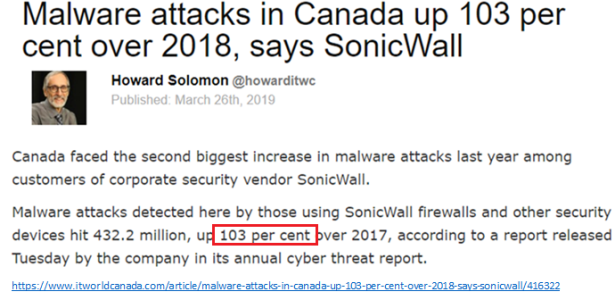
- Then number of Malware attacks in Canada rose by 103 per cent over 2018.
- Statistics Canada says the national rate of police-reported extortion from cyber-crime rose 44 per cent in 2018.

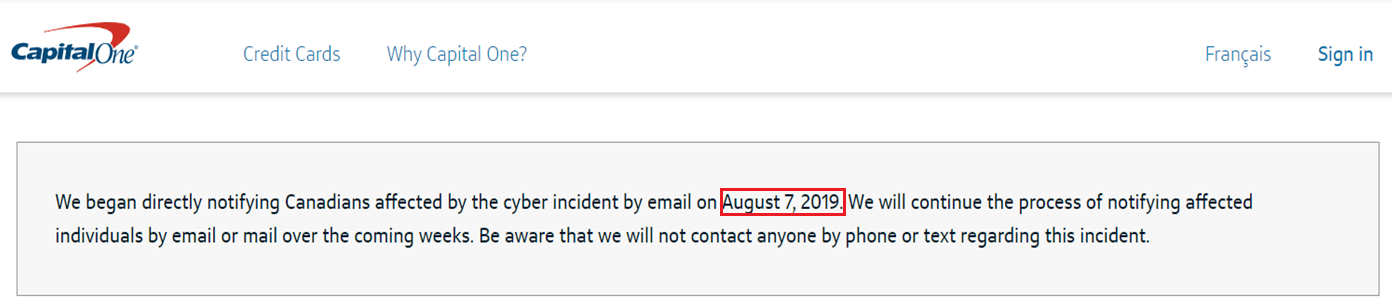
Even big corporations with strong security are subject to breaches. You may have seen in the news that CapitalOne was recently breached:
Why is this happening?
- The nature of cyber-crime has been changing over the past several years. The concept of a “hacker” sitting at his computer typing furiously is no longer accurate.
- Most cyber-crime attacks are now automated (via “bots” and other distribution code).
- A hacker (or a group of hackers) will design code to exploit weaknesses in software security, remote systems access (firewall ports\RDP) or more commonly take advantage of people’s lack of diligence when responding to\reading emails and then they will deploy it “out to the web”.
- They are typically deployed through Phishing-email on a huge scale… like the “spam” email you get every day.
- In most cases, it is not a “Targeted” attack – anyone can be at risk, particularly small businesses as they often lack the dedicated internal IT staff to actively protect against Viruses and to educate users on best-practices to use to help reduce the risks.
- As a result, any Company – big or small – is at risk.
- In response to this, the Federal government has opened the Canadian Centre for Cyber Security website (https://cyber.gc.ca/en/)
- Yet breaches continue to occur daily. Many companies still do not (or are unable to) allocate sufficient resources nor have the required knowledge to properly protect themselves.
- Businesses now also have the responsibility to report certain breaches to the Government as per “PIPEDA”:
- The Personal Information Protection and Electronic Documents Act (PIPEDA) outlines the responsibilities of corporations to notify individuals in the case of a breach.
- The Federal Government further ratified this with additional requirements which came into November 1, 2018 (http://www.gazette.gc.ca/rp-pr/p2/2018/2018-04-18/html/sor-dors64-eng.html)
What does the future hold?
- No one can predict the future, especially when it comes to technology, however trends would indicate that we can expect to see cyber-crime threats expand in diversity and perhaps use other mediums for delivery such as social media networks, LinkedIn, Twitter, etc. in addition to the common “email” spams.
- In response to this, we can also expect to see an increase in the adoption of “duo-authentication” security packages – where authentication is handled by a combination of mediums: e.g. a logon screen on your PC followed by a confirmation button on your phone\mobile device. Duo-Mobile is one such example, though there are others.
- There will likely be an increase in the number of Cyber-security companies we see, offering various improved Anit-virus\Anti-breach software
- And we will see more and more companies migrating to Cloud-based systems as they can provide a degree of greater security than on-premise one.
However, at the end of the day the real protection is diligence and educating your staff.
The Dark Web – What you should know about what’s really out there
Some background…
- In the summer of 2016, the world’s corporate networks became easier targets when the National Security Agency (NSA) had their clandestine hacking tool kit stolen by a hacker group called “The Shadow Brokers” who have since made these tools public.
- This toolkit exploited security holes that vendors knew nothing about and allowed the “Shadow Brokers” to infiltrate
- The Dark Web is where this (and other such groups) maintain their presence and “do their work”
Essentially, the Dark Web is the “Black Market” of the Internet
- Most “hackers” will get what they want in the form of a Ransom. Then the data that is obtained (userids\passwords, etc.) are “sold” in the Dark Web.
- In some cases the “hacker” will just take your information and never notify you and they will sell it in the Dark Web. That information is then used by others for various purposes.
- Often, it is a year or two after they obtain your information that they will then “put it on the market”.
- You could be breached and never know it.
What you can do Right Now to help mitigate your risk
-
Your first best defense are your people
- Educate your staff so they are aware of how to protect themselves and the company against threats
- Never directly open any attachment in an email, skype or text. IF you think it might be safe then download it to your PC and run it from the PC. Most breaches occur from this simple act.
- READ pop-ups\messages that appear on your screen and do not just click “yes”. Be aware of what you are responding to, even if it looks harmless.
- Give thought to any responses you are thinking of making to pop-ups, warnings, emails, etc. Does it really make sense? Look at the link you are being asked to visit – does it seem legitimate. If in doubt, do a quick Google search on it – odds are if it is a scam others have likely fallen for it and there will be posts\warnings
-
Revisit and Implement new Password policies
- All employees should be responsible for remembering (and changing) their own Passwords. IT staff should not be the “keepers of the passwords”. Make your people part of the solution
- Use different passwords for different programs AND Do not “Save” your passwords nor use the “remember me” options on devices.
- Separate Business from Personal passwords (especially with Social Media – Facebook, LinkedIn, Twitter, etc.). IF you do get hacked in one at least the other will not also be hacked
- Enforce password complexity settings and regular password changes – for example:
- Passwords must be 8 characters on more
- Passwords must contain a mix of Upper and Lower characters and at least 1 non-alpha-numeric character:
- Passwords will expire every 3 months – that’s 4 times per year
- The last 4 passwords are “remembered” by the system and cannot be reused in that time
- Do not send passwords via Email and do not include all the details in electronic communications. For example, send remote connection information without pwds in an email and then skype or text or phone in the pwds
-
Make sure you have a Backup and Disaster Recovery Plan in place
- 35% of on-premise backups fail (you cannot restore from them). Either due to old media being used, or a damaged sector on a drive, or the fact that they simply having not been maintained or tested.
- Backups are CRITICAL and yet it is the most often over-looked or underestimated aspect of Business systems.
- At least twice a year, perform a full “Test Recovery” of your systems to ensure that it not only works but that you are aware of all of the steps and have a sense of how long it will take
- Document the Backup and Recovery processes – in case your IT is not available when disaster strikes
- Ensure you backup to External media (not just to another drive on the server) AND ensure you have off-site backups – whether it be drives that are disconnected or online backups to co-locations sites. There are many companies which can offer online offsite backup services.
- Ensure you have multiple levels of backup: Do not just backup your Virtual Servers to external media, you should also be backing up your Database backup files AND any key
-
Consider using “Service Accounts” to run key Systems\Services
- Allows you to change the passwords for “logon” accounts (or even disable them) in the event of a breach without impacting your systems directly.
-
Patch your systems regularly
- Microsoft does a lot to help prevent breaches – it can be annoying at times but it is in your company’s best interest to apply them.
- This goes hand-in-hand with periodic scheduled rebooting of your servers to ensure items are applied fully and to further ensure the systems restart properly
-
Combine Anti-Virus programs and Anti-Malware programs on your systems.
- Anti-Virus programs alone are not enough – use them in combination with Anti-Malware programs (Malwarebytes, etc.)
-
Schedule regular scans and where possible a launch a manual scan at the end of each week.
-
Consider End-point security for on-line systems
- Even if you are using “on-line” or Cloud-based systems you are still using PCs\devices to connect to those systems and you are still subject to potential “end-point” breaches.
- Do not assume that because something is “on-line” or “in the cloud” that you are completely safe from threat
-
Ensure you have “Exit procedures” in place for when Employees leave
- While we never think of ex-employees as being a threat it can and does happen. It can even happen “innocently” where passwords or access information is discovered after a person has left the company and perhaps is not as diligent as they should be
- Ensure you have a policy for deactivating ex-employee accounts from the Domain, Dbases and any software packages upon their exit. IF they had access to “Admin” accounts then have a process for changing the passwords for those as well. This also protects the ex-employee as they can legitimately claim they had no access
-
Consider next-level anti-breach software …
- There are Next-Generation Anti-breach packages which use Artificial Intelligence to examine code in programs before it is even executed.
- Pro-active as opposed to the Re-active “Virus Definitions” from most AV programs
-
Be Prepared for what you don’t know – you may already be “hacked” and not even know it
- Make sure to have a breach response plan especially if you use web based applications or cloud services that could leave you exposed.
- Be diligent – regular updates and scans. Review router logs and Event Viewer messages. If you see odd behaviour then follow up on it.
If in doubt, contact VOX ISM. If you think you have been hacked but are unsure, remove your systems from any internet\remote access (including your own wifi) and contact VOX ISM .
VOX ISM can help too…
3 levels of Security options by VOX ISM

-
Enhanced Security & End-point Protection
- PCs (end-point users) are the #1 source of breaches
- This package fortifies your end-points through a layered defense approach with unified prevention, multi-stage detection and automated response
- Applies to Cloud-based users as well as On-premise systems
- Protects physical and virtual desktops & servers with Windows, MAC and Linux OS
- Provides intuitive interface for managing settings and configurations for On-line systems along with pre-configured “template” profile settings that allow for prevention and early-warning of possible insecure settings within On-line systems
-
Secure Backup Protection
- 35% of on-premise backups fail (you cannot restore from them). Either due to old media being used, or a bad sector on a drive, or simply not maintained\tested
- The Secure Backup protection offers secure Off-site backups to ensure safety of backups and recoverability.
- Applies to Databases and key files\folders for On-premise
- For Cloud-based systems, this includes the backup of O365 Email, Sharepoint and OneDrive files. Dynamics365 users (CRM\BC) already have their Databases backed up by MS in the Cloud.
- Guards against Ransomware corruption of backups as well as physical damage (flood\fire, etc.)
- Flexible pricing based on usage is available (based on 50GB\mnth packets)
-
Managed Security & Prevention Services
- Designed for improved Data-loss prevention
- Utilizes Advanced Virus and Spam protection including Artificial-Intelligence-based AV protection software
- Protects all end-point devices (PCs, Servers, routers etc.)
- Includes Policy-Driven Encryption to help protect against “data mining”
- Applies to On-line\D365 users as well as On-premise with Windows, MAC and Linux OS
- Allows for early warnings of potential system issues
Final Comments:
Contact us for one of our 3 Security Packages to protect your systems now.
Implement Internal Security Policies and Procedures right away!
- Train your staff on the importance of being diligent
- Develop a Password Change and Complexity policy and change your passwords … soon
- Have your IT develop a “Disaster Recovery Plan” – not just for Security breaches but for other “disasters” – what is being backed up and where? Do you have all that you need?
Contact VOX ISM if you are not sure where to start or what to do. We would be more than happy to assist you!
Check VOX ISM’s event page for weekly free events. We have 67 events in the second half of 2019.
Blog post by Trevor Reid – Senior Technology Consultant, VOX ISM

With over 25 years of experience in the Software and IT Industries (and 20 years with VOX ISM), Trevor has been involved in hundreds of software implementations and upgrades. Currently, he is VOX ISM’s “go to” resource for anything technical having to do with SQL Server, SharePoint, Mobility/IFD, Remote Access, Database migrations and other areas of IT infrastructure and administration. Trevor works closely with our customers and their IT personnel and is always eager to share his wealth of knowledge.